firewall and security
Firewall and Security: Safeguarding Your Digital Fortress
In an era where cyber threats loom large and data breaches are a constant threat, the role of firewalls in ensuring digital security cannot be overstated. Firewalls serve as the first line of defense against malicious entities seeking to infiltrate computer networks and compromise sensitive data. In this comprehensive article, we will delve into the world of firewalls and security, exploring their significance, types, implementation, and their crucial role in safeguarding digital assets.
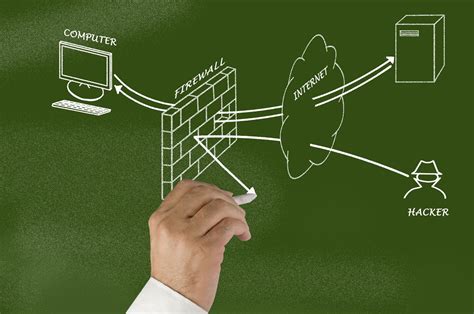
The Anatomy of a Firewall
Before we dive into the depths of firewall security, it’s essential to understand what a firewall is and how it functions. At its core, a firewall is a network security device or software that acts as a barrier between a trusted internal network and untrusted external networks, such as the internet. It monitors incoming and outgoing network traffic, permitting or blocking data packets based on a set of predefined security rules.
Packet Filtering Firewalls
Packet filtering firewalls are the most basic type of firewall. They operate at the network layer (Layer 3) of the OSI model and make decisions based on criteria such as source and destination IP addresses, source and destination ports, and the protocol used (e.g., TCP, UDP). These firewalls are fast and efficient but lack the deep inspection capabilities of more advanced firewall types.
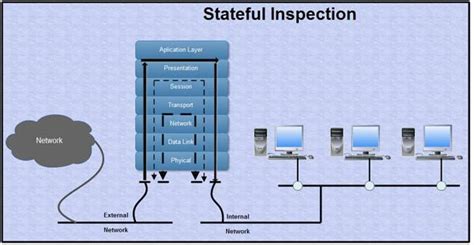
Stateful Inspection Firewalls
Stateful inspection firewalls, also known as dynamic packet filtering firewalls, are an evolution of packet filtering firewalls. They keep track of the state of active connections and make decisions based on the context of the traffic. This allows them to provide better security by understanding the state of the connection and not just individual packets.
Firewall Implementation: Hardware vs. Software
Firewalls can be implemented in two primary forms: hardware and software. Each has its own advantages and use cases.
Hardware Firewalls
- Hardware firewalls are standalone devices specifically designed to protect a network.
- They are typically deployed at the perimeter of a network, between the internal network and the external internet.
- Hardware firewalls provide robust security and are less vulnerable to attacks targeting the host operating system.
- They are suitable for larger organizations with complex network infrastructures.

Software Firewalls
- Software firewalls are applications or programs that run on individual devices, such as computers or servers.
- They are ideal for protecting individual devices and are commonly used on personal computers.
- Software firewalls can be customized to specific user preferences and applications.
- They are more cost-effective for small businesses and individual users.

Advanced Firewall Features
Modern firewalls come equipped with a plethora of advanced features that enhance their security capabilities.
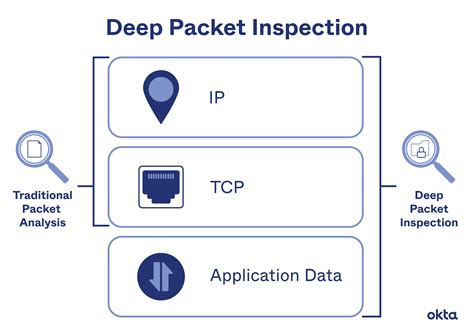
Deep Packet Inspection (DPI)
Deep Packet Inspection is a technology that allows firewalls to inspect the content of data packets at a granular level. This means they can identify and block specific types of content, such as malware, viruses, or certain applications, even if they use non-standard ports.
Intrusion Detection and Prevention Systems (IDPS)
IDPS is a crucial feature that helps firewalls detect and respond to suspicious or malicious activities in real-time. These systems can not only block malicious traffic but also generate alerts and logs for further analysis and investigation.
Firewalls in Action: Case Studies
Let’s explore two real-world case studies to understand how firewalls have played a pivotal role in preventing cyberattacks and protecting sensitive data.
Case Study 1: Sony Pictures Hack (2014)
In 2014, Sony Pictures Entertainment fell victim to a devastating cyberattack that exposed sensitive company data and led to a massive data breach. The attackers, believed to be linked to North Korea, used a combination of malware and social engineering tactics to gain access to Sony’s network. However, it was revealed that Sony’s firewall security measures were outdated and ineffective, allowing the attackers to breach their defenses easily.
Outcome: Sony Pictures suffered substantial financial losses and reputational damage. This incident highlighted the importance of regularly updating and maintaining firewall systems to protect against evolving cyber threats.
Case Study 2: Equifax Data Breach (2017)
In 2017, Equifax, one of the largest credit reporting agencies in the United States, experienced a massive data breach. Hackers exploited a known vulnerability in the company’s website software, gaining access to sensitive personal information of over 147 million individuals. Equifax had failed to apply a critical software patch that would have protected against this attack, highlighting a critical oversight in their firewall and security strategy.
Outcome: The Equifax breach led to widespread outrage and calls for improved cybersecurity practices. It underscored the importance of regularly patching vulnerabilities and maintaining robust firewall defenses.

Firewall Best Practices
To maximize the effectiveness of firewalls in protecting your digital assets, consider the following best practices:
- Regularly update firewall rules and configurations to adapt to evolving threats.
- Implement a strong password policy for firewall access to prevent unauthorized changes.
- Combine firewall technologies with other security measures, such as intrusion detection and prevention systems.
- Train employees to recognize and report suspicious activities that might bypass the firewall.
- Conduct regular security audits and penetration testing to identify vulnerabilities.
The Evolving Landscape of Firewall Security
As technology advances and cyber threats become more sophisticated, the role of firewalls in security continues to evolve. Here are some emerging trends in firewall security:
Next-Generation Firewalls (NGFWs)
NGFWs combine traditional firewall features with advanced security technologies, such as application-layer filtering and threat intelligence. They provide deeper visibility into network traffic and offer better protection against modern threats.
Cloud-based Firewalls
With the migration of services and data to the cloud, cloud-based firewalls have become increasingly popular. They provide security for cloud environments and offer scalability, making them suitable for businesses of all sizes.
Conclusion
In an interconnected world where cyber threats are ever-present, firewalls stand as formidable guardians of our digital fortresses. These essential security devices and software applications act as sentinels, defending against malicious entities seeking to breach our networks and compromise our data. To ensure robust protection, organizations must deploy and maintain firewalls effectively, keeping pace with the evolving threat landscape and adopting best practices in cybersecurity.
Remember, the importance of firewalls cannot be overstated. They are the first line of defense, and a strong firewall strategy can mean the difference between security and vulnerability in today’s digital age.
Q&A
1. What is the primary purpose of a firewall?
The primary purpose of a firewall is to act as a barrier between a trusted internal network and untrusted external networks, such as the internet. It monitors and controls incoming and outgoing network traffic to prevent unauthorized access and protect sensitive data.
2. What are the different types of firewalls?
There are several types of firewalls, including packet filtering firewalls, stateful inspection firewalls, proxy firewalls, next-generation firewalls (NGFWs), and cloud-based firewalls. Each type has its own strengths and use cases.
3. What are some best practices for firewall security?
Some best practices for firewall security include regularly updating firewall rules, implementing strong password policies, combining firewalls with other security measures like intrusion detection systems, training employees to recognize suspicious activities, and conducting regular security audits.
4. How do next-generation firewalls (NGFWs) differ from traditional firewalls?
NGFWs combine traditional firewall features with advanced security technologies, such as application-layer filtering and threat intelligence. They provide deeper visibility into network traffic and offer better protection against modern threats compared to traditional firewalls.
5. Why is it crucial to keep firewall systems updated?
Keeping firewall systems updated is crucial because cyber threats are constantly evolving. Regular updates help ensure that firewalls can effectively defend against new and emerging threats, vulnerabilities, and attack techniques.
6. How can organizations improve their firewall security strategy?
Organizations can improve their firewall security strategy by staying informed about the latest cybersecurity threats, adopting best practices, conducting regular security assessments, and investing in modern firewall technologies like NGFWs and cloud-based firewalls.
