waf network security
The Crucial Role of WAF Network Security in Protecting Your Digital Assets
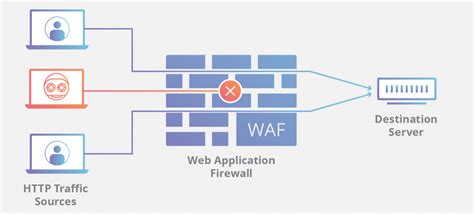
In today’s digital age, where businesses and individuals rely heavily on the internet for various activities, security breaches and cyber threats have become more prevalent than ever. Protecting digital assets, sensitive data, and customer information is paramount. One essential component of a robust cybersecurity strategy is Web Application Firewall (WAF) network security. This article explores the critical role of WAF network security in safeguarding your online presence, its benefits, real-world applications, and why it’s a must-have for businesses in today’s cybersecurity landscape.
The Growing Cybersecurity Threat Landscape
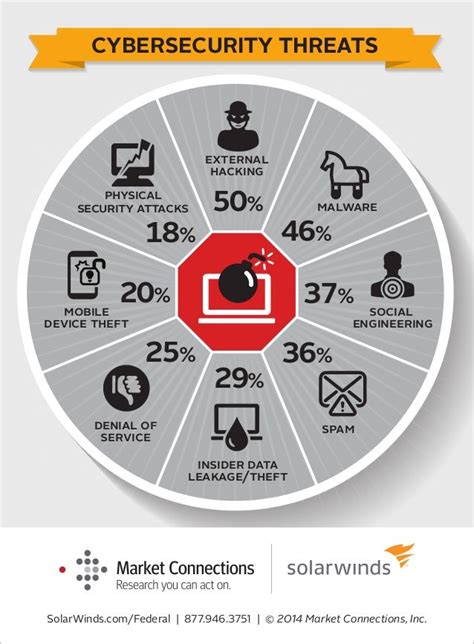
The digital world is a dynamic and interconnected space, but it’s also fraught with dangers. Cybersecurity threats have evolved to become more sophisticated, and attackers continuously seek new ways to exploit vulnerabilities. Here are some concerning statistics that highlight the severity of the issue:
- In 2020, there were 3,932 confirmed data breaches, resulting in the exposure of 37 billion records. (Source: Statista)
- Ransomware attacks increased by 62% in 2020, with the average ransom payment reaching $178,254. (Source: Cybersecurity and Infrastructure Security Agency)
- The global cost of cybercrime is projected to reach $6 trillion annually by 2021. (Source: Cybersecurity Ventures)
These alarming figures underscore the urgent need for effective cybersecurity measures, including robust WAF network security solutions.
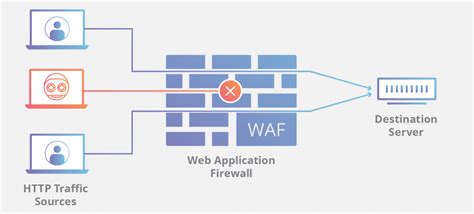
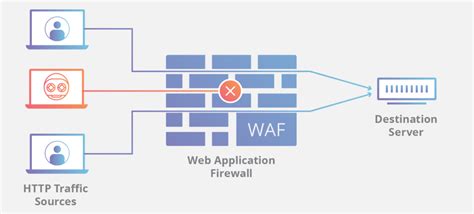
What is Web Application Firewall (WAF) Network Security?
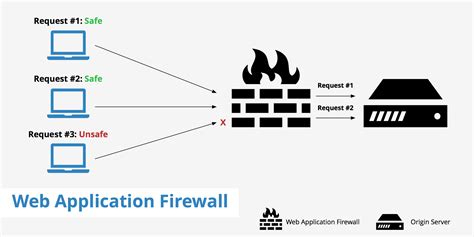
A Web Application Firewall, or WAF, is a security solution designed to protect web applications and websites from various online threats. It acts as a shield between your web applications and potential attackers, monitoring and filtering incoming traffic to block malicious requests and safeguard your data. Key features of WAF network security include:
- Access Control: WAFs control who can access your web applications and what actions they can perform.
- Protection Against Common Vulnerabilities: They defend against common web application vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
- Rate Limiting: WAFs can limit the number of requests from a single IP address to prevent DDoS attacks.
- Real-time Monitoring: They continuously monitor web traffic and detect suspicious activities in real-time.
- Logging and Reporting: WAFs provide detailed logs and reports for analysis and compliance purposes.
Why WAF Network Security is Crucial

1. Protection Against OWASP Top 10 Vulnerabilities
The Open Web Application Security Project (OWASP) publishes a list of the top 10 most critical web application security risks. These include well-known threats like injection attacks, broken authentication, and security misconfigurations. WAFs are instrumental in mitigating these risks by identifying and blocking malicious requests that exploit these vulnerabilities.
2. Prevention of Data Breaches
Data breaches can have devastating consequences, both financially and in terms of reputation. WAFs help prevent data breaches by thwarting attempts to steal sensitive information, such as customer data, credit card numbers, and login credentials. They provide an additional layer of defense beyond traditional network security measures.
3. Mitigation of DDoS Attacks
Distributed Denial of Service (DDoS) attacks can overwhelm your web servers, rendering your online services inaccessible. WAFs can detect and mitigate DDoS attacks by limiting the number of requests from a single IP address or employing other rate-limiting techniques. This ensures that your web applications remain available to legitimate users even during an attack.
4. Enhanced Compliance
Many industries have stringent compliance requirements, such as the Payment Card Industry Data Security Standard (PCI DSS) or the Health Insurance Portability and Accountability Act (HIPAA). Implementing a WAF can help your organization meet these requirements by providing the necessary security controls and generating compliance reports.
Real-world Applications of WAF Network Security
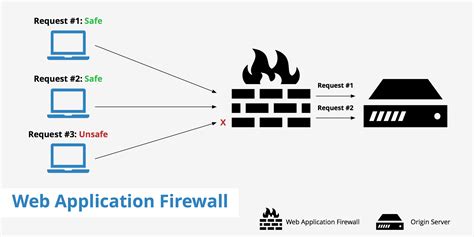
WAF network security is not just a theoretical concept; it has real-world applications across various industries. Let’s explore some examples:
1. E-commerce
Online retailers face a constant threat of cyberattacks, especially during peak shopping seasons. WAFs protect e-commerce websites by blocking malicious bots, preventing credit card fraud, and ensuring the integrity of customer data. This allows shoppers to browse and make purchases with confidence.
2. Healthcare
The healthcare industry handles sensitive patient information and must comply with strict privacy regulations. WAFs help healthcare organizations secure patient portals, electronic health records (EHRs), and telemedicine platforms, ensuring that patient data remains confidential and secure.
3. Financial Services
Banks, investment firms, and financial institutions rely on WAFs to safeguard online banking applications, trading platforms, and customer accounts. By preventing account takeovers and financial fraud, WAFs protect both the institution and its clients.
4. Government and Public Sector
Government agencies and public-sector organizations often serve as targets for cyberattacks due to the valuable information they hold. WAFs play a critical role in defending government websites and digital services against cyber threats, ensuring public trust and national security.
Challenges and Considerations
While WAF network security offers numerous benefits, it’s essential to be aware of the challenges and considerations when implementing it:
1. False Positives
WAFs can sometimes flag legitimate traffic as malicious, leading to false positives. Fine-tuning the WAF rules and regularly reviewing logs can help minimize this issue.
2. Evolving Threats
Cyber threats are constantly evolving, and attackers are finding new ways to bypass security measures. Regular updates and staying informed about emerging threats are crucial.
3. Resource Intensive
Implementing a WAF can be resource-intensive, both in terms of hardware and personnel. Organizations must
allocate sufficient resources to maintain and monitor their WAF effectively.
4. Expertise Required
Configuring and managing a WAF effectively requires cybersecurity expertise. Organizations may need to invest in training or seek external support to ensure optimal protection.
Choosing the Right WAF Solution
When selecting a WAF solution for your organization, consider the following factors:
1. Scalability
Ensure that the WAF can scale with your organization’s growth and handle increased web traffic without compromising performance.
2. Integration
Choose a WAF that seamlessly integrates with your existing cybersecurity infrastructure, including your firewall, intrusion detection system (IDS), and security information and event management (SIEM) tools.
3. Customization
Look for a WAF that allows you to customize rules and policies to suit your specific application and security requirements.
4. Support and Maintenance
Consider the availability of vendor support, software updates, and maintenance services to ensure the long-term effectiveness of your WAF.
Conclusion
In a digital landscape teeming with cyber threats, Web Application Firewall (WAF) network security stands as a formidable defense against malicious actors. By protecting against common vulnerabilities, preventing data breaches, mitigating DDoS attacks, and enhancing compliance, WAFs play a pivotal role in safeguarding your digital assets and maintaining your organization’s integrity.
As businesses and individuals alike rely increasingly on web applications and online services, investing in WAF network security is not just a smart move; it’s a necessity. By understanding the importance of WAFs, their real-world applications, and the challenges they entail, organizations can make informed decisions to fortify their cybersecurity posture and stay ahead of the evolving threat landscape.
Remember, in the ever-evolving world of cybersecurity, proactive protection is the key to a secure digital future. Choose the right WAF solution, invest in expertise, and stay vigilant to ensure your online presence remains safe and resilient in the face of emerging threats. Your digital assets and your reputation depend on it.
Q&A
If you have any questions or would like further information about WAF network security, feel free to ask. Your cybersecurity is our priority.
